24 years’ experience in professional IT support
Qualified IT experts supporting hundreds of organisations around the UK
99.4% customer retention rate
Flywheel IT Services offers fully managed Zero Trust cyber security, to help businesses and other organisations to eliminate high costs, complexity and vulnerabilities.
Adantages of the ZTEdge platform
Quick & Easy
Flywheel can get the ZTEdge platform up and running in minutes, accelerating your organisation’s move to Zero Trust security
Comprehensive & Consistent
Zero Trust security controls are enforced across your distributed network
Always There
Flywheel's 24/7 support service means your organisation is protected anytime, anywhere, on any device
Affordable
Priced for smaller organisations, ZTEdge packages cost significantly less than comparable competitor products
What is the concept behind the Zero Trust cyber security framework?
Cyber attacks are worse than ever
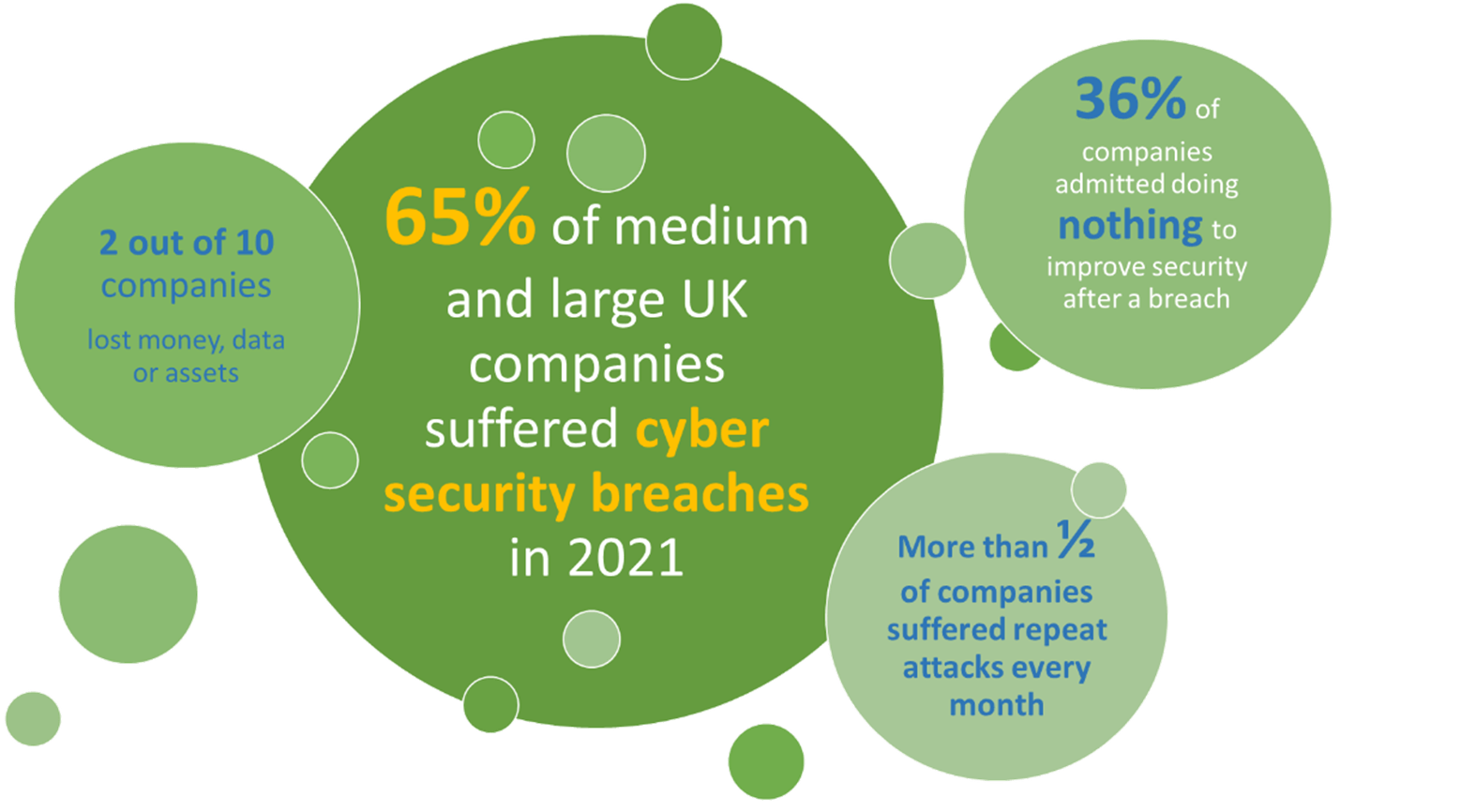
Did you know that a quarter of UK companies suffer at least one cyber attack every single week of the year? A third of them admit doing nothing about it. This leaves them at risk of breaking GDPR or other laws specific to their business or professional activities.
Zero trust makes checks throughout the network
Zero Trust does away with the old concept of a network with a perimeter, and users being trusted once inside. It assumes risk is an inherent factor, both inside and outside the network.
Instead of the “trust but verify” method, the new Zero Trust model improves security and reduces risk by requiring that all users are authenticated, authorised, and continuously validated. As tools evolve and change, Zero Trust is quickly becoming the new security standard for our work environment.
UK Cyber attack statistics 2021 (SOURCE: UK Government)
Who is Zero Trust cyber security for?
It is ideal for all organisations to have a Zero Trust model in place. It’s particularly important for organisations that have higher than average compliance and legal standards to maintain. This includes financial services, insurance, healthcare, legal, government bodies and any organisation that holds data on individuals for whom safeguarding may be an issue.
Flywheel also strongly recommends Zero Trust to companies that have already suffered a cyber security breach and know they need to harden their security.
“
“Never trust, always verify”
John Kindervag, Zero Trust creator & Forrester Research security analyst.

ZT Edge: the enterprise quality platform for smaller and midsize companies
What is the ZTEdge Zero Trust suite?
The Zero Trust suite, built by Ericom, comprises around 20 different products that Flywheel can configure according to your organisation’s security needs, and fit around the IT solutions you already have.
At Flywheel, we always offer the best value solutions we can find. We recommend ZT Edge as the best option for cutting edge security with cost-conscious pricing. Two of the most important elements provide safe web browsing and secure remote working.
Web dangers blocked: the Ericom ZT Web Isolation Gateway
The web is a key tool for most types of work. It also remains the number one attack vector for malicious actors to take a business offline and steal information.
Ericom’s ZT Web Isolation Gateway prevents zero-day exploits, such as ransomware, phishing attacks and malicious code in documents. This means your employees can use and interact with web content without fearing that the next click will be the one which hurts your business.
Remote access concerns resolved: Ericom ZTNA
Historically, organisations were office-based and security was designed with users being centrally located behind a perimeter. The perimeter became the protection layer and, once inside, verified users were trusted: outside bad, inside good.
Cloud adoption, however, and increasing numbers of remote-working organisations have led to huge changes and benefits in productivity, cost and access. Today’s workers can be anywhere, on any device. This cultural shift needs a new security strategy. The perimeter concept no longer applies, with assets and resources both inside and outside networks. Not only can users be anywhere, they can use whatever device they choose.
Credential theft is a huge problem, too. Typically, organisations are set up in a way that means if a user has their identity or passwords stolen, the hacker can access all of a business’ applications and resources. This means they will be able to see and harm everything, either by deploying ransomware or by stealing the secrets that help your business thrive.
By using a strategy of ‘least privileged access’, modern online businesses today are turning to Zero Trust Network Access (ZTNA) to reduce opportunities to attack, and dramatically reduce the impact of credential theft. ZTNA moves your business from ‘trusted users’ to ‘least privileged access’, which means users are only given access to the applications and resources they need to perform their work. All other systems and resources are made invisible.
If a user is compromised, the attacker will no longer be able to move laterally around your network, so reducing the impact of the breach.
How does Zero Trust work?
A user’s identity is verified by ZTEdge, and they are then granted access to the applications and resources they need.
Micro-segmentation ensures each individual user only sees the tools and applications they need for their work. If your user doesn’t need it, not only can they not try to log into it, they cannot see it.
Advanced technologies which help deliver Zero Trust include:
- DNS security
- CASB
- Secure Web Gateway
- Antivirus
- IDS IPS
- Identity and access management
- Cloud firewall
- Ransomware prevention
- SSL inspection
These are all backed up with access to a multi-vendor threat intelligence network.
In the event of a threat, ZTEdge isolates the user. This prevents credential theft but still enables documents to download safely.
It also isolates the applications, verifies users, validates devices and limits privileged access.
Implementing ZTEdge Zero Trust for cyber security
Flywheel makes using Zero Trust easy. We deliver the cloud-native platform working closely with your in-house IT team. We offer flexibility, preferring a modular approach rather than “rip and replace”. This means anything you have already invested in will not go to waste.
We provide a fully managed service with our 24/7 Security Operations Centre (SOC). Our SOC constantly monitors your Zero Trust network to identify suspicious activity and threats. The ZTEdge devices are fully integrated into our SIEM & SOAR platforms to give you the fastest response to issues and alerts.
If we identify any threat, our Cyber Security Incident Response Team will minimise the impact. We will put our highly trained and experienced experts to work instantly.
How much will Zero Trust cost my organisation?
Most modules of the ZTEdge portfolio have been deliberately priced to cost significantly less than competing products which offer comparable functionality. Ericom designed ZT Edge to give the best security possible to smaller, cost-conscious organisations.
The price you pay will partly depend on:
- The functionality you need
- The number of users you have
- Other cyber security products that you already have
We would be very happy to discuss your cyber security concerns and analyse how your company works, then identify the ideal solution for you and give you a breakdown of the costs.
About Us
Flywheel IT Services has teams of highly qualified and experienced IT engineers and consultants around the UK.
For over 20 years we have partnered with businesses, schools and major construction companies to provide IT services and to guide and support their IT projects, tech strategies and day-to-day operations.



